Did you know that cybercriminals can freely send emails pretending to be your boss, an organization you trust, or even your bank in order to hack you? This is an example of a phishing attack, which is popular among hackers.
Your emails need proper DNS (Domain Name System) settings to make sure that they are delivered where they need to go. But when these settings are wrong, it’s easy for malicious actors to impersonate trusted email domains to scam other users.
The good thing is that you can stop hackers from hijacking your email domain using a special kind of DNS setting called DMARC.
But as simple as that sounds, we were shocked to find that 41% of the banking institutions worldwide do not have DMARC set up for their domains.
Our research examined DMARC coverage for Fortune 500 companies, other major global companies across various sectors, and government sites worldwide. And as we show below, the results are extremely worrying.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email authentication protocol that domain owners can use to define how receiving servers should handle emails claiming to be sent from their domain. It enables organizations to protect their domains from unauthorized use and keep their customers safe from phishing attacks.
To understand some of the findings of this research, it may be helpful to get familiar with DMARC policies. There are 3 types of DMARC policy options that a domain can choose from:
These include:
- ‘reject‘ questionable messages (meaning they simply won’t reach the recipient’s mailbox at all)
- ‘quarantine‘ them (meaning the messages are sent to the spam folder)
- and ‘none‘ (meaning no action is taken to block unauthorized emails, leaving the recipient vulnerable to phishing attacks).
You can jump to any section of this post by using the quick links below:
- Quick Summary – Key Findings on the State of Email Security
- Banking Domains Remain Vulnerable
- Global Companies Negligent in Domain Protection
- Government Domains Dangerously Susceptible Worldwide
- Fortune 500 Companies Better Committed to Email Security
- US State Agencies Lag Behind the Global South
- Oceania Companies Lead the Way
- Safeguarding the Future of Email Security
Quick Summary – Key Findings on the State of Email Security
We examined DMARC coverage trends across industries, countries, and government levels. Our findings are hugely worrying across the board.
Here’s what we discovered:
- An alarming 41% of the domains from the banking sector had no DMARC protocols set up. Other industries fared even worse, with 91% of the domains from the graphic design sector lacking DMARC.
- 66% of the largest global companies from various industries had domains with no DMARC protection.
- Overall, only 35% of the domains attached to government organizations from 198 countries had DMARC enabled, leaving the vast majority of citizens vulnerable to email fraud.
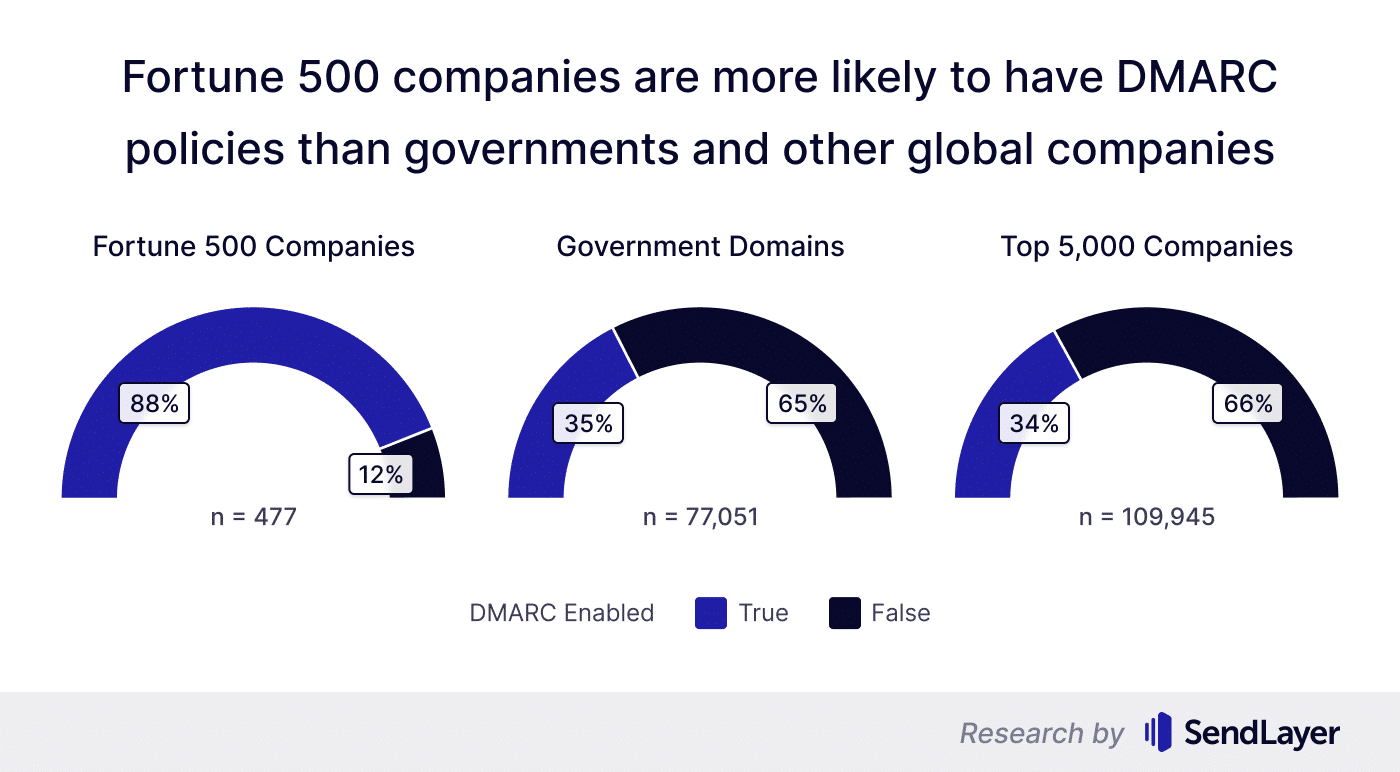
- 12% of Fortune 500 companies had no DMARC protocols in place. Although Fortune 500 companies’ domains were more likely to have DMARC enabled than other groups of domains, many thousands of customers of these companies are still vulnerable to attack
- In the US, as much as 60% of the government domains we examined had no DMARC protocols.
- By region, company domains from Oceania are the most likely to have DMARC enabled followed by Europe, the Americas, Asia, and Africa.
- We observed no connection between the GDP or population size of a country and DMARC coverage of its government or company domains.
Pretty alarming, right?
That’s just the tip of the iceberg. Let’s dive into these statistics in detail to see how far this problem goes.
Banking Domains Remain Vulnerable
DMARC coverage trends vary wildly by industry. But we found even sensitive sectors like banking have a dangerously low level of DMARC adoption.
41% of the banking institutions were unprotected by DMARC. Although the banking industry is more likely than other sectors to implement DMARC protocols, it still leaves countless customers vulnerable to financial fraud carried out using fake emails.
Overall, it's very concerning that as much as 41% of the domains in the banking industry have no DMARC set up.
Despite so many domains lacking DMARC, the banking sector had the highest DMARC coverage compared to other sectors we examined. Yet in an absolute sense, the level of protection in banking is far from adequate.
It's quite easy for scammers to imitate an unprotected banking domain and trick people into transferring large sums of money.
The state of email domain security is even worse in other sectors. Insurance and law firms are the only other sectors with 50% or more DMARC coverage, while aviation, semiconductor, computer software, and financial services industries scored just slightly above 45%.
It’s clear that the sectors with relatively high DMARC coverage (like banking and insurance) are those at significant risk of phishing scams. Neglecting robust email security protocols can prove highly damaging to such industries with serious risks to their customers.
In some sectors, DMARC usage is dangerously uncommon. We found that only 9% of the domains from the graphic design industry had DMARC protection, the lowest among all.
Religious institutions, fundraising, and art and craft also had some of the worst DMARC coverage proportions.
While these sectors aren't as frequently targeted by hackers, it's still hugely risky for small companies to ignore basic email security protocols like DMARC.
Recovering from a scam is much harder than the measures needed to prevent it.
Global Companies Negligent in Domain Protection
We also examined the largest global companies outside of the Fortune 500 (F500), and we found the worst DMARC coverage trends in this group.
Over 66% of the domains attached to the top global companies outside of the F500 didn't have DMARC set up. Among the companies with DMARC enabled domains, more than half had their policy set to 'none', meaning that no action would be taken to stop suspicious emails. This leaves customers vulnerable to phishing attacks carried out in the company's name.
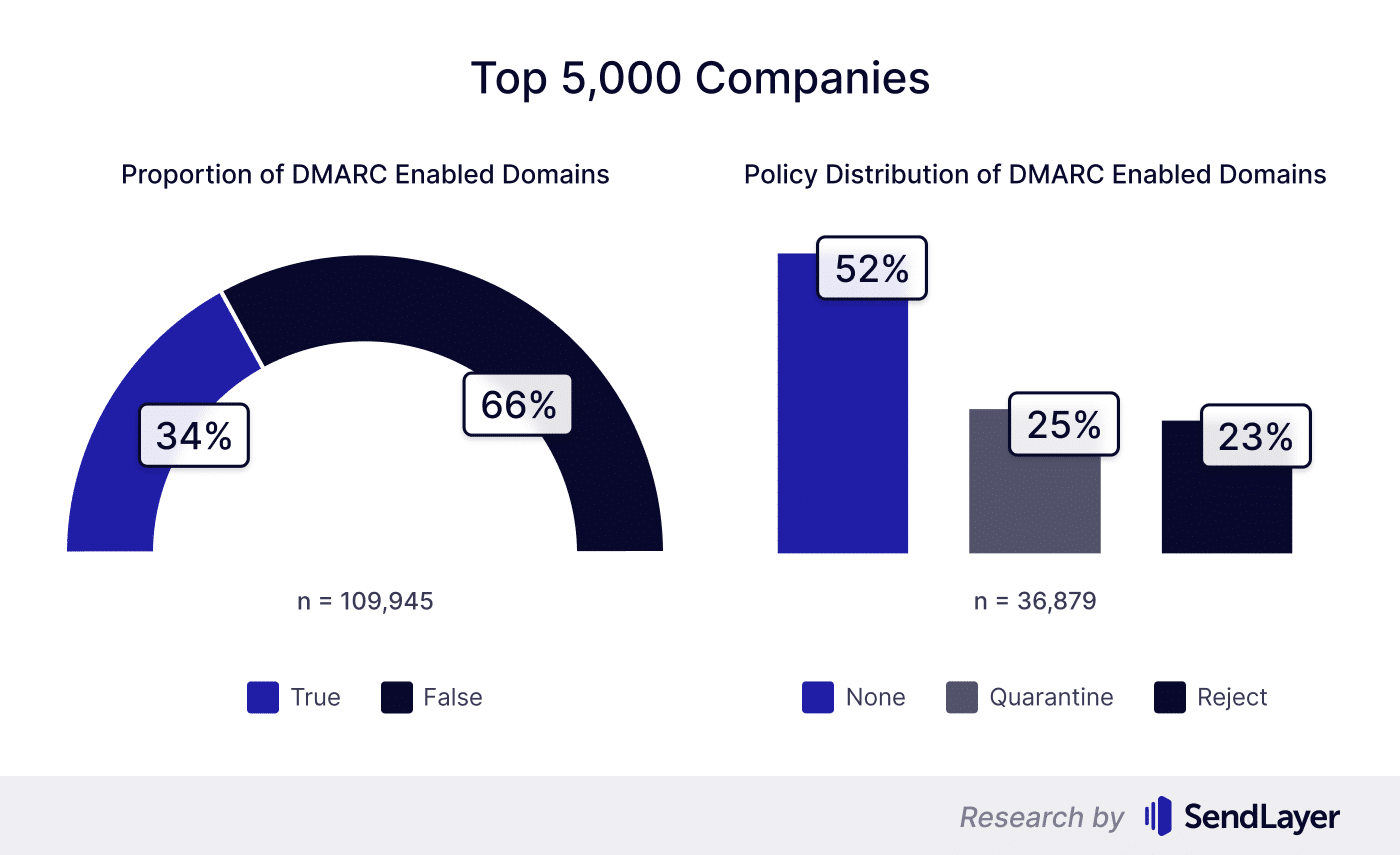
The dataset for this part of the analysis includes the largest 5,000 companies by employee size per country across 67 different countries.
Among the 109,954 domains attached to these global companies, 66% had no DMARC protocols.
To make matters worse, we observed that 52% of the company domains that did have DMARC were using a policy of 'none'. As a result, no action would be taken by mail servers if an unauthorized message is sent, allowing hackers to scam employees and customers by impersonating the company domain.
Government Domains Dangerously Susceptible Worldwide
Globally, government agencies displayed a poor commitment to setting up DMARC protocols, leaving millions susceptible to phishing attacks.
65% of the government domains we examined from 198 countries had no DMARC protocols. Phishing attacks imitating government agencies are particularly dangerous because they're much more likely to be trusted by individuals.
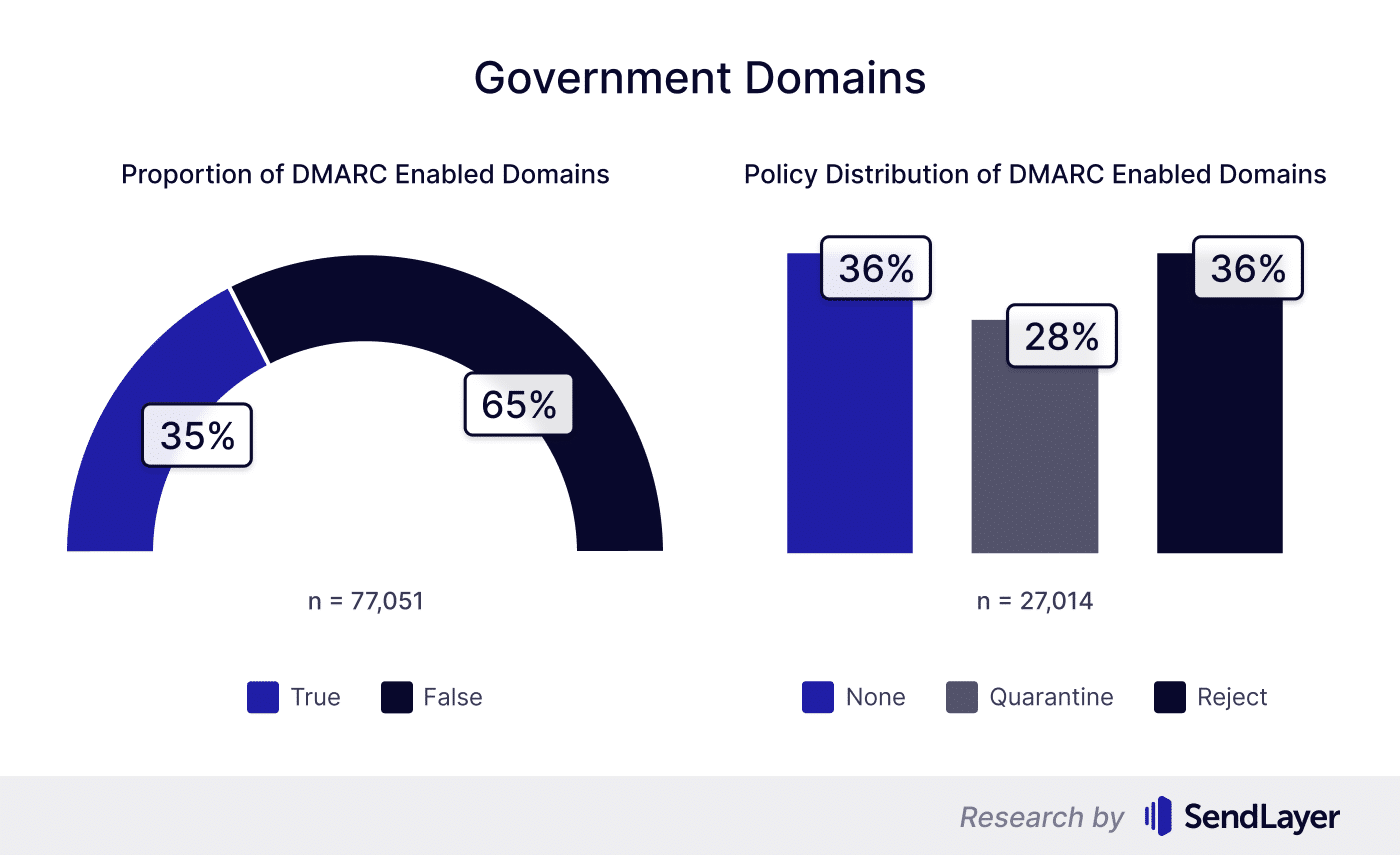
With 65% of the 77,051 government domains in our dataset having no DMARC protection, there's a huge security gap for hackers to take advantage of.
It's worth noting that among the government domains with DMARC protocols in place, about 36% were using a policy of 'none'. Using the 'none' policy isn't ideal, so it's good that a smaller proportion of domains in this group uses it compared to other groups we studied.
Yet the overall low DMARC coverage levels in public domains across the world remain a worrying trend.
State institutions have a responsibility to protect individuals from scams run in their names. Unfortunately, only a few smaller countries had near-perfect DMARC coverage rates.
Togo and Armenia both had 100% of their state domains protected by DMARC. But both countries have very few government domains (2 and 4, respectively), which makes them outliers in our research.
Malta and Moldova stood at 97% DMARC coverage, and these countries have a larger number of active government domains (29 and 87, respectively).
While it's easier to take security measures when a country only has a few domains to protect, we didn't find a clear correlation between the number of public domains and DMARC coverage trends for countries at the state level.
Fortune 500 Companies Better Committed to Email Security
The Fortune 500 is far from foolproof when it comes to email domain security.
Despite having the highest DMARC coverage collectively, the companies representing Fortune 500 still had 12% of the domains with no DMARC protection.
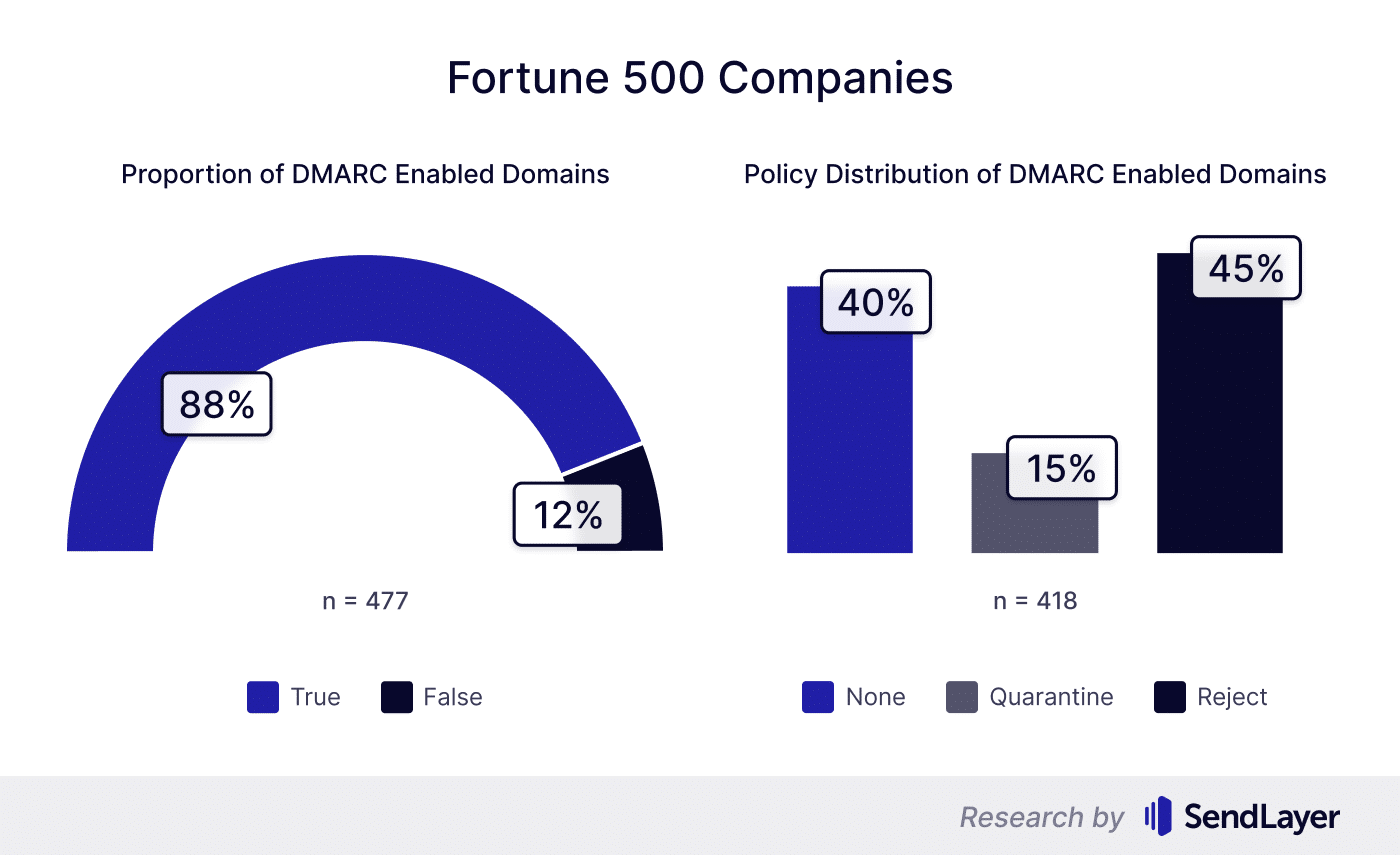
We were able to check the DMARC records of 477 companies representing the Fortune 500 published in Fortune magazine for the 2021-2022 period.
Even though 12% of the companies from F500 didn't have DMARC records at all, F500 still collectively boasts the highest DMARC coverage of all groups of domains (global companies and governments) from our dataset.
While 88% DMARC coverage is an impressive number, we should bear in mind that F500 includes some of the most well-resourced companies in the world. As such, these companies should be expected to push for DMARC coverage higher than 95%.
Analyzing further, we discovered a more worrying trend. Among the F500 companies that had DMARC records added, 40% had their policies set to ‘none’. Because a 'none' policy is unsafe, hackers can freely spoof these company domains to send phishing emails to customers.
It’s possible that the domains having no DMARC set up or using the ‘none’ policy may be using some other email security measures that we didn’t track.
But considering the effectiveness of DMARC when set up properly, we think it’s unlikely that the domains shying away from using DMARC have a more reliable system in place in every case.
US State Agencies Lag Behind the Global South
US public domains displayed lower than ideal DMARC coverage, ranking even worse than some technologically challenged countries.
60% of the US government domains had no DMARC protection. This is worse than the DMARC adoption trends in some under-resourced countries including Afghanistan, Uganda, Ethiopia, and Kenya.
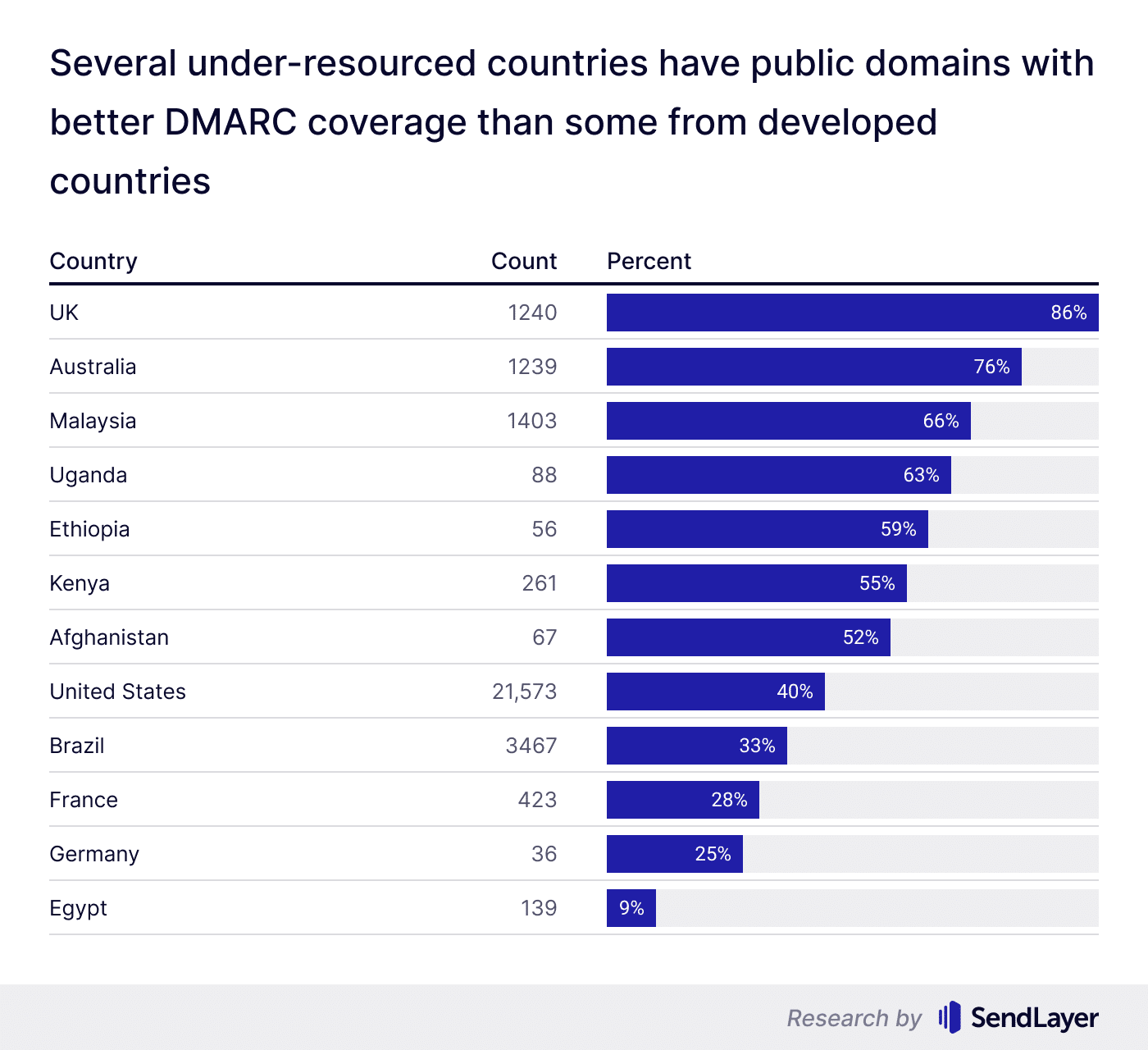
The US was outranked in DMARC coverage of public domains by countries from unlikely regions. Several smaller countries and underdeveloped nations like Afghanistan, Uganda, Ethiopia, and Kenya had significantly better DMARC adoption than the US.
However, the US is not alone in this. Leading nations like France and Germany were among many that fared even worse regarding DMARC coverage of public domains.
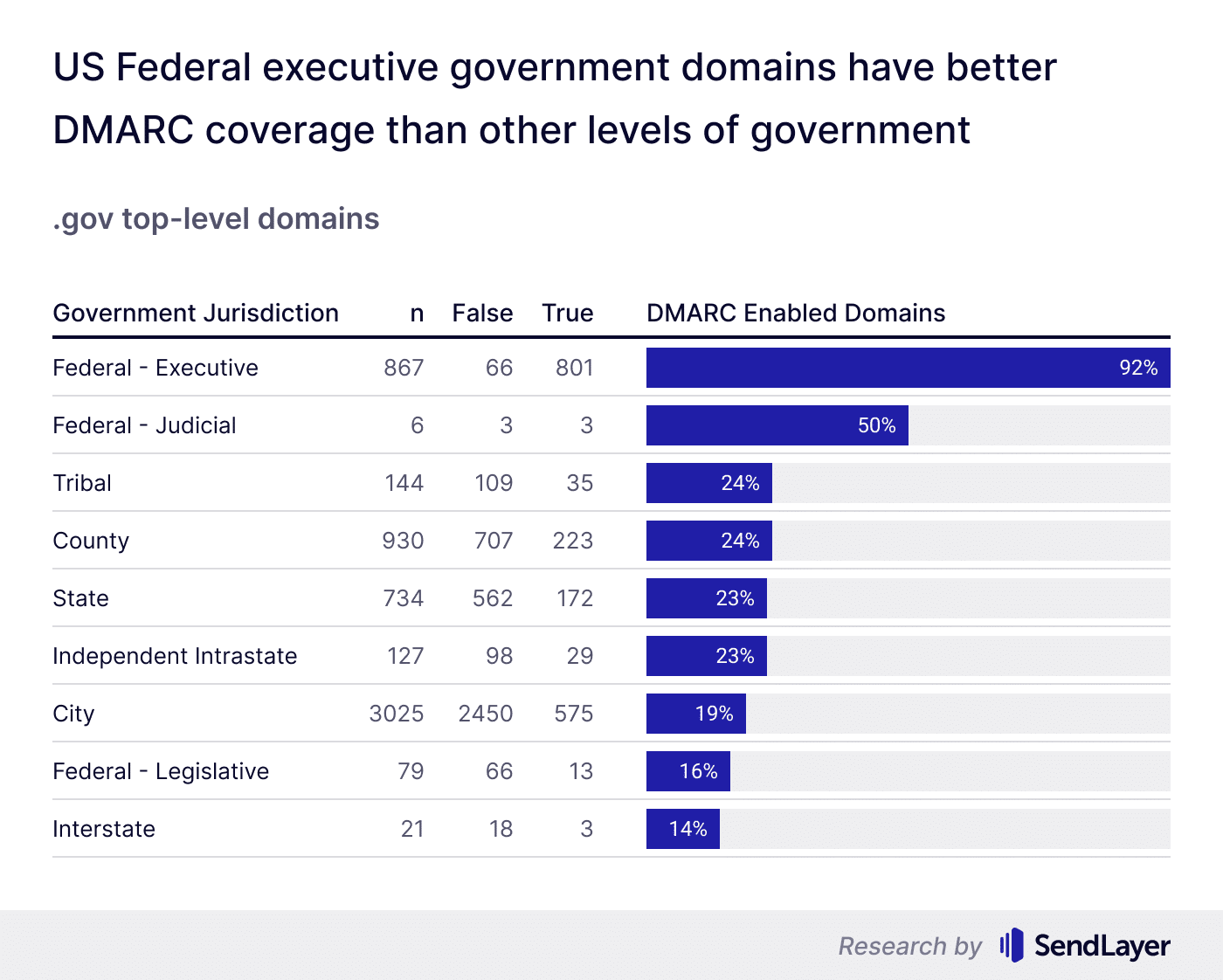
We further analyzed the DMARC adoption trends by level of government in the US.
Unsurprisingly, the federal-executive domains ranked the highest in terms of DMARC coverage at 92%, with federal-judicial standing at 50%. In contrast, interstate government domains ranked the lowest, having DMARC set up for only 14% of their domains.
We also analyzed the US government sites outside of the top-level .gov domains.
Once again, we found domains owned by the federal government having the best DMARC coverage at 35% (though still dangerously low in absolute terms).
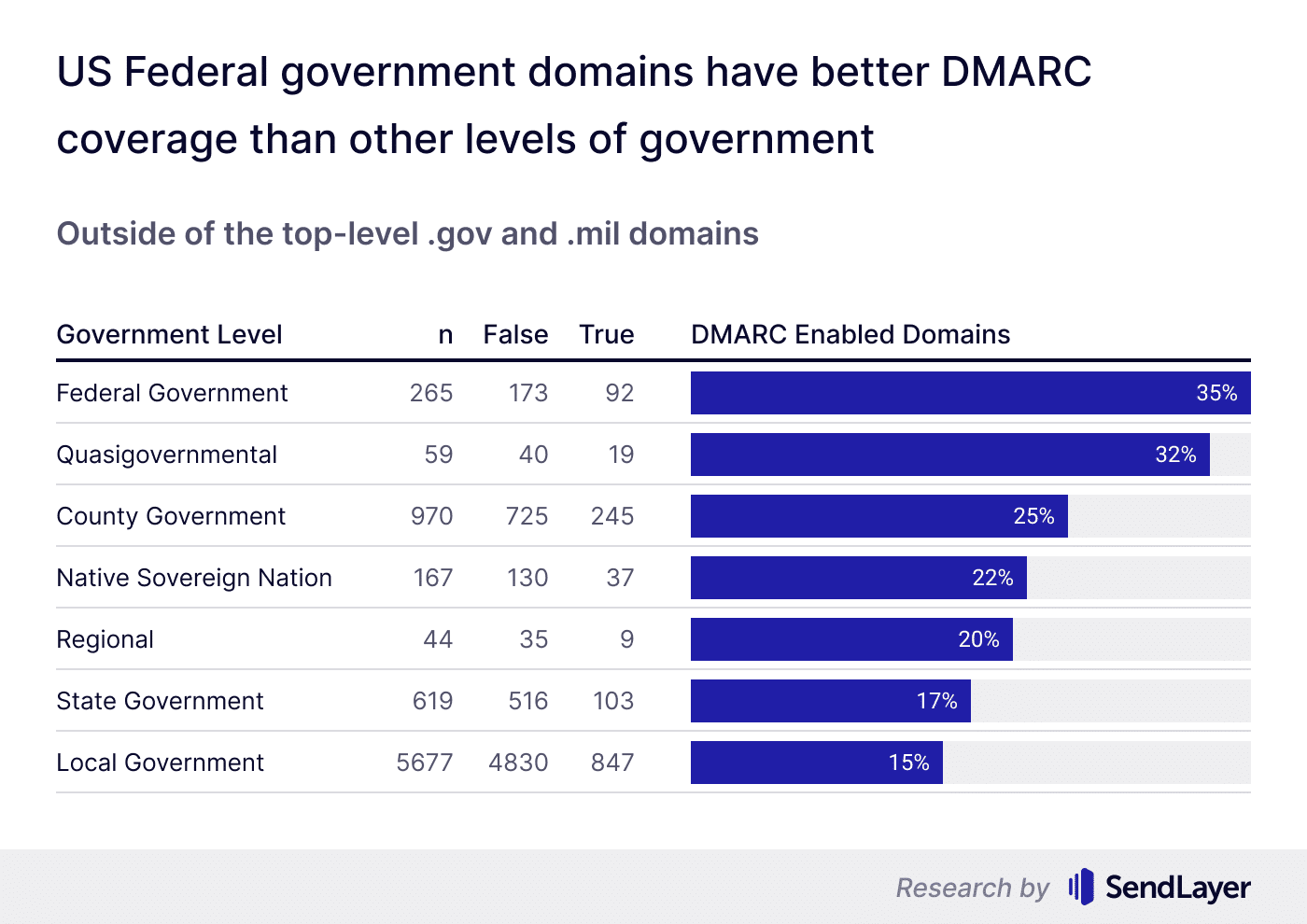
On the other end of the spectrum, the local government sites had the worst DMARC utilization at only 15%.
At the state level (sites both within and outside .gov top-level domains), Washington, DC had the best DMARC coverage at 80%, with Maryland being the only other state scoring higher than 50%.
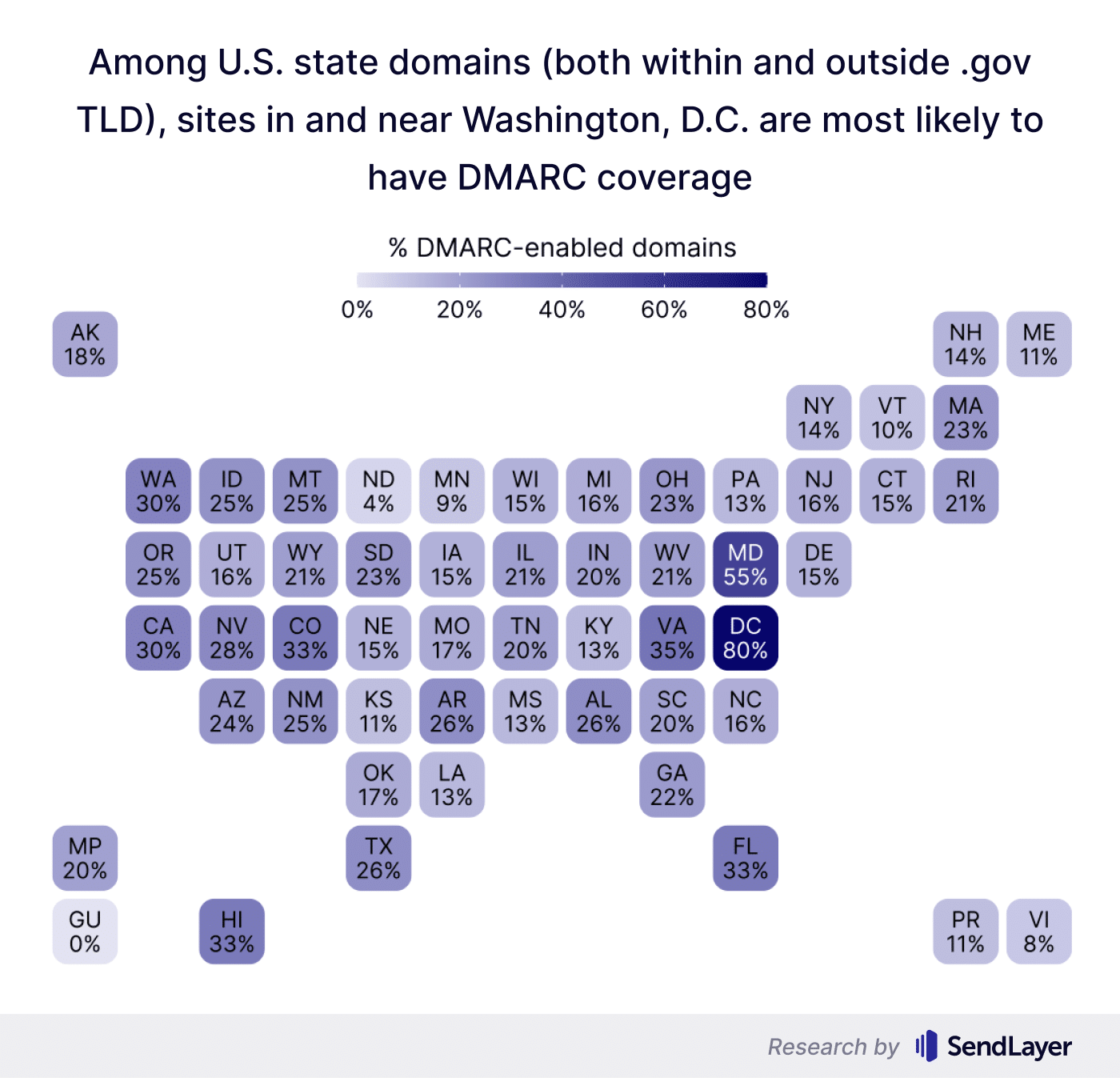
Overall, the state of email security in US government domains is not very promising.
This is despite the US Department of Homeland Security issuing an order in 2018 mandating the use of DMARC for all federal agencies.
Interestingly, the US also has the largest number of government domains at 21,573.
While the large number of domains can complicate DMARC implementation, the US is still a highly well-resourced country. It's reasonable to expect the US to display a stronger commitment to protecting its government domains and keeping citizens safe from email phishing.
Note: Our research only checked DMARC records for public-facing web domains with the assumption that these usually match the domains used for emails. But it's possible that some government institutions may be using a separate email domain that doesn't match their public-facing web domain. Even in this case, it's important for organizations to protect both kinds of domains because scammers can still launch convincing phishing attacks capable of tricking even careful users using a recognizable government or company domain.
Oceania Companies Lead the Way
Lastly, we analyzed DMARC coverage trends of major companies by country and region, uncovering some interesting findings.
Overall, companies from regions with better IT resources and online security awareness like Oceania and Europe were more likely to use DMARC than companies from under-resourced areas, including Africa and Asia. By country, companies from Denmark had the highest DMARC coverage at 59%, with companies from the US coming second at 53%.
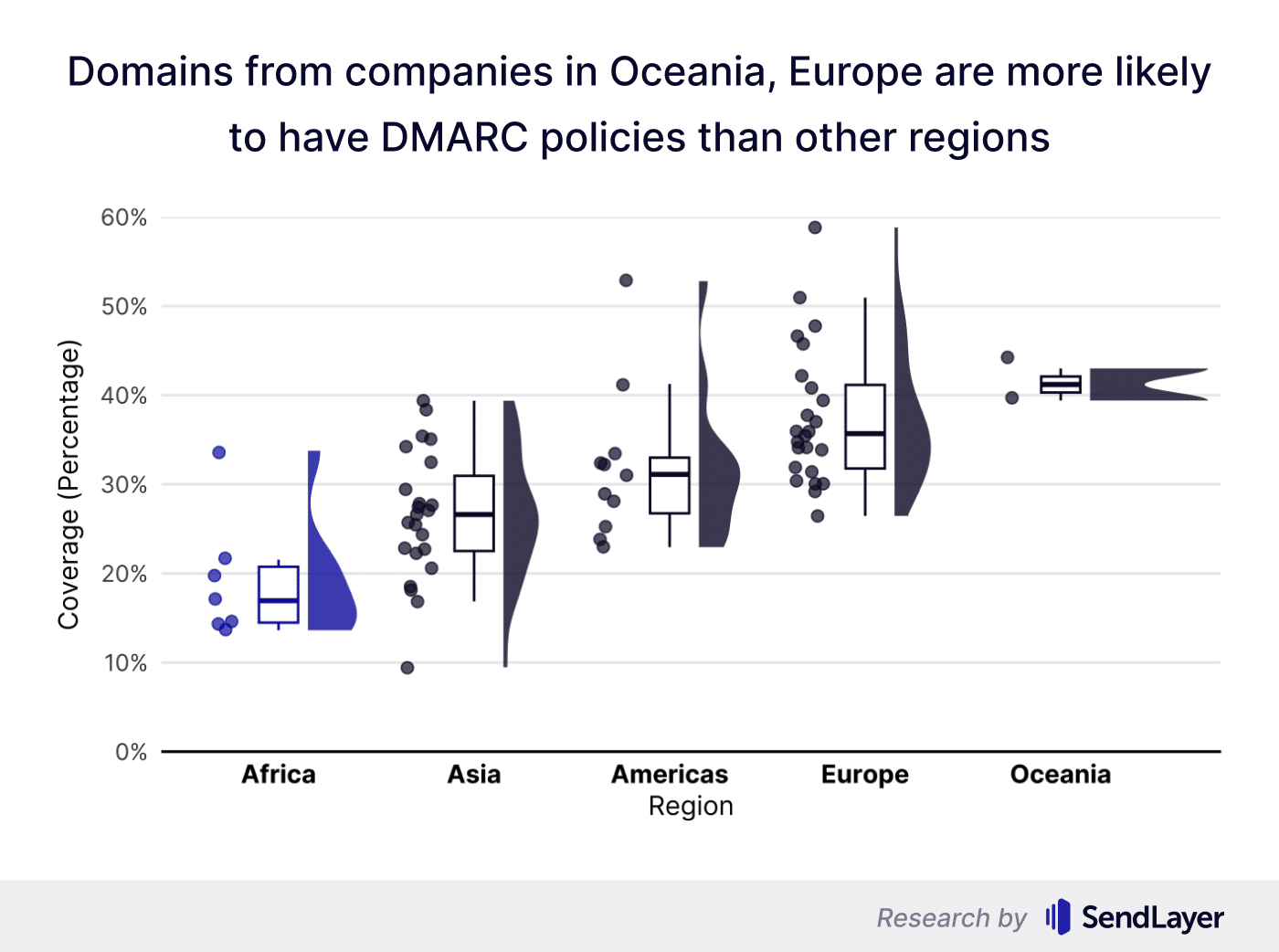
At the regional level, domains from Oceania had the most impressive DMARC coverage, ranking at the top.
European countries rank second, followed by the Americas, Asia, and Africa.
These results aren’t surprising. Oceania and Europe have the technological infrastructure to implement strong email security policies across companies.
The situation is markedly worse for technologically under-equipped regions. Many parts of Asia and Africa lack the resources to practice good online security consistently, leading to wider gaps in DMARC adoption.
At the country level, Denmark stands the highest, with DMARC coverage of 59%.
The US occupies the 2nd highest spot even though almost half of the country's company domains lack DMARC protocols.
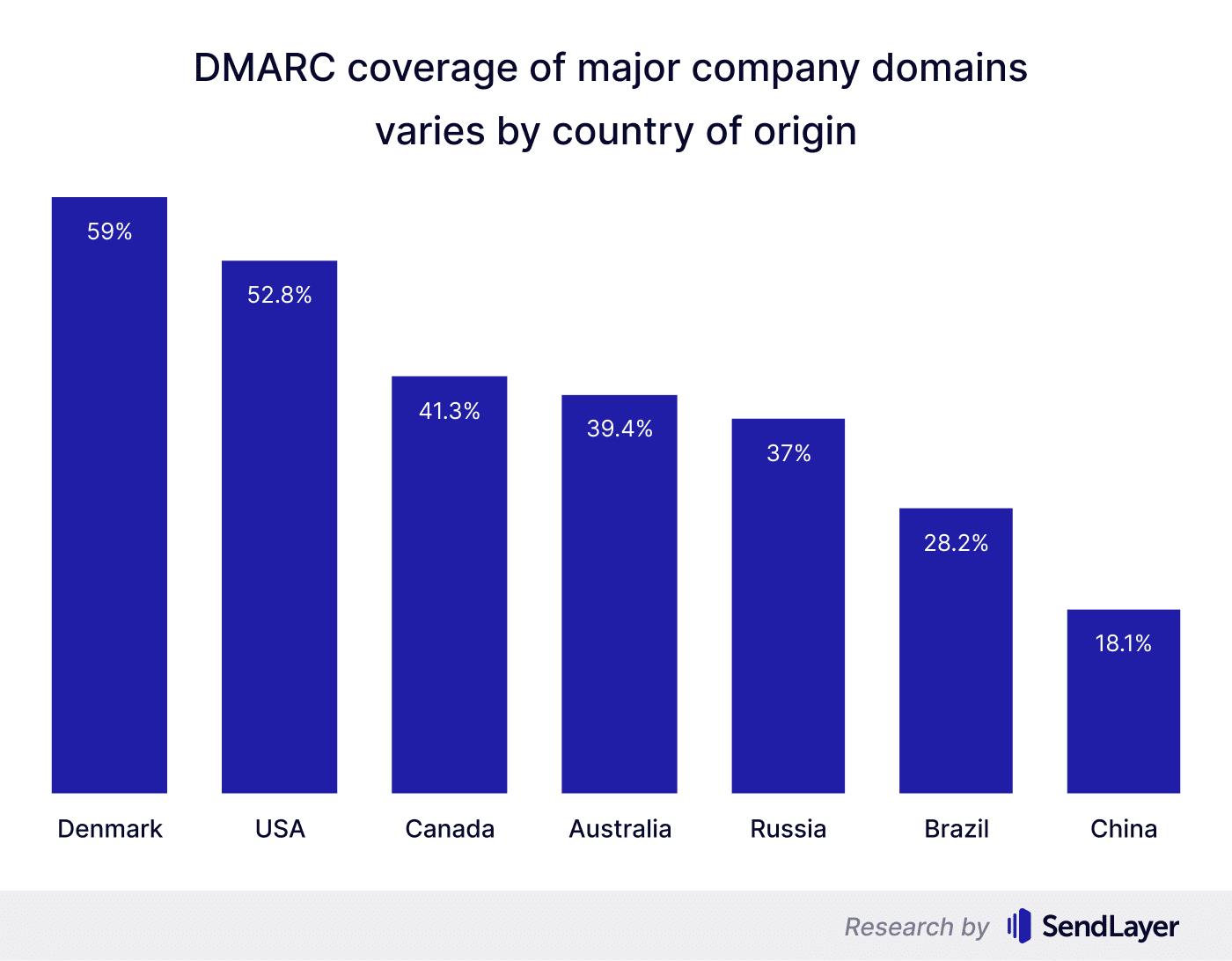
Note that even at its best, the DMARC coverage for individual countries only went as high as 59%. This is far from the levels required to curb email scams.
These statistics indicate an essentially negligent attitude from companies from even the leading nations of the world when it comes to taking adequate anti-phishing measures.
Interestingly, we observed no relationship between the GDP or population size of a country and DMARC coverage trends in its largest 5,000 companies.
Safeguarding the Future of Email Security
Phishing and email fraud are some of the oldest and most prevalent forms of online scams. Yet organizations and government agencies all over the world have continued to disregard email security measures to protect users from phishing threats.
We think governments worldwide should establish strong official policies for all state domains to have DMARC enabled to combat phishing.
For companies, an email scam imitating their domain can cause a serious reputational crisis and erode public trust. The cost of these risks should alone serve as an incentive to adopt more robust email security measures, starting with DMARC as the first line of defense.
Gmail and Yahoo both announced earlier this year that they would be requiring messages sent to users of their email services to be authenticated using protocols such as SPF, DKIM, and DMARC by early 2024. The wide influence of these companies should hopefully have a positive effect in encouraging more organizations to adopt DMARC.
As a secure transactional SMTP service, we make it mandatory for SendLayer users to set up DMARC for their accounts to protect their domains. Sign up today to get started.
Is your company vulnerable? Send this article to your IT team and ask them to check if they have their DMARC set up correctly. Together, we can do our part to help keep the internet safe.
Methodology: For this analysis, our team first checked whether domains will load successfully without any errors (HTTP status code 200), including redirected domains (status code 301). Then, we checked DMARC protocols using a Python tool. The raw data is available in this Google sheet.
Caveats: Our analysis may have missed some companies for which the domain used for emails doesn’t match the public-facing web domain, which we checked. Also, while we checked the DMARC results multiple times, false negatives may be present in the analysis, given protection against raw requests and browser emulation.

0 comment on "We Analyzed the Email Security Protocols of 187,482 Organizations. Here’s What We Found."